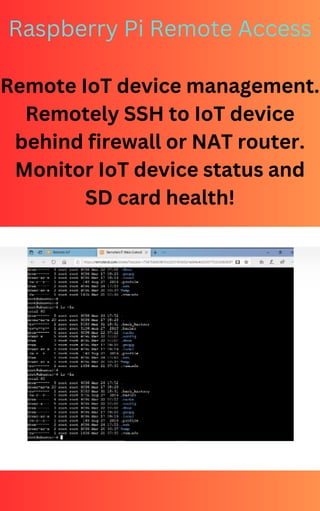
Is secure remote access to your IoT devices a necessity, or a vulnerability waiting to be exploited? The answer is clear: without robust remote access protocols, your IoT infrastructure is exposed to significant risks, and the ability to remotely manage and troubleshoot devices is severely hampered.
In the rapidly evolving landscape of the Internet of Things (IoT), the ability to securely and efficiently manage devices from afar is not just a convenience—it's a critical requirement. As IoT deployments expand in scope and complexity, spanning everything from smart homes and industrial automation to environmental monitoring and healthcare, the need for secure remote access solutions becomes paramount. Implementing remote access allows for essential maintenance, troubleshooting, and data retrieval without the need for physical presence, drastically improving operational efficiency and reducing downtime. However, the inherent nature of remote access also introduces vulnerabilities. Without proper security measures, these remote connections can become gateways for malicious actors seeking to compromise your devices and networks. Therefore, the choice of remote access protocols, the implementation of robust security practices, and the selection of appropriate hardware and software are vital decisions for anyone deploying IoT technologies.
Let's delve into the core of this crucial technology.
| Feature | Details |
|---|---|
| Purpose of SSH in IoT | SSH provides a secure channel for remotely accessing and managing IoT devices, enabling secure command execution, data transfer, and troubleshooting. |
| Encryption | SSH employs robust encryption algorithms to protect data transmitted between the user's device and the IoT device, safeguarding against eavesdropping and data breaches. |
| Authentication | SSH offers multi-factor authentication (MFA) and supports password and SSH key-based authentication, significantly enhancing security by verifying user identities. |
| Remote Command Execution | Authorized users can execute commands on the IoT device remotely, which allows for configuration changes, software updates, and diagnostic checks. |
| Secure Tunneling | SSH tunneling enables secure communication through firewalls and gateway routers, providing a protected connection between local and remote devices. |
| Commonly Used Tools | OpenSSH is a widely used open-source implementation, known for its flexibility and security. |
| Suitable Devices | Raspberry Pi 4, Arduino Portenta H7, and ESP32-S3 are examples of devices that offer excellent options for secure remote access. |
SSH, or Secure Shell, is the backbone of secure remote access in the IoT domain. Its primary function is to establish a secure, encrypted connection between a user's device and a remote server or device, providing a reliable method for accessing and managing IoT devices from any location. This is accomplished through a combination of cryptographic techniques, including strong encryption algorithms, secure authentication mechanisms, and the ability to execute commands remotely. The implementation of SSH in an IoT environment dramatically improves the operational efficiency and security posture of the deployment. Rather than physically accessing each device for maintenance, updates, or troubleshooting, authorized personnel can perform these tasks remotely, saving time, resources, and reducing the risk of human error. Furthermore, the encrypted nature of SSH communication protects sensitive data from being intercepted or tampered with during transit, enhancing the overall security of the IoT ecosystem.
The significance of SSH in the realm of IoT remote access cannot be overstated. As IoT deployments become more complex and distributed, the need for a secure and reliable remote management solution becomes ever more pressing. SSH delivers on this need, offering several key advantages: Encrypted Communication: SSH utilizes robust encryption algorithms to protect data transmitted between the user and the IoT device. This safeguards against eavesdropping and data breaches, ensuring that sensitive information remains confidential. Strong Authentication: SSH supports multiple authentication methods, including passwords, SSH keys, and multi-factor authentication (MFA). This provides strong identity verification, preventing unauthorized access to the IoT device. Remote Command Execution: Authorized users can execute commands on the IoT device remotely, enabling them to configure settings, update software, and perform diagnostic checks from anywhere. These combined features make SSH an indispensable tool for securing and managing IoT devices in a wide range of applications.
However, the implementation of SSH alone is not enough to guarantee complete security. Several best practices must be followed to minimize vulnerabilities and maximize the effectiveness of SSH in an IoT environment. The best approach begins with strong passwords or the use of SSH keys. Instead of relying on easily guessable passwords, it is highly recommended to implement SSH key-based authentication, which is significantly more secure. SSH keys are cryptographic keys that are used to authenticate users without the need for a password. The use of long, complex passwords and the regular changing of those passwords are also recommended, if using that method. Implement multi-factor authentication (MFA) to require a second form of verification, such as a one-time code generated by an authenticator app, in addition to the password or key. MFA adds an extra layer of security and makes it much more difficult for attackers to gain access to a device. Regularly update SSH software and any other related software to patch security vulnerabilities. Security flaws are often discovered in software, and updating to the latest version ensures that any known issues are addressed. Use a firewall to control network traffic to and from the IoT devices. Firewalls can restrict access to only authorized IP addresses and ports, limiting the attack surface. Configure SSH to run on a non-standard port. This can help to make it more difficult for attackers to find the SSH service. Regularly monitor SSH logs for any suspicious activity. This can help to detect and respond to potential security breaches.
SSH tunneling is another critical technique for enhancing the security of IoT remote access. It is a method of creating an encrypted connection between two devices, allowing secure communication through firewalls and gateway routers. SSH tunneling allows you to create secure tunnels for transferring data between local and remote devices. This is particularly useful when accessing devices behind a firewall or on a private network. Here's how SSH tunneling works. The user establishes an SSH connection to a server, known as the SSH server. This connection is encrypted using the SSH protocol. Once the SSH connection is established, the user can then use the SSH server as a proxy to access other resources, such as websites or other devices, on the remote network. All traffic that is sent through the tunnel is encrypted, ensuring that it is protected from eavesdropping. This can be especially useful in environments where IoT devices are behind firewalls or on private networks, allowing remote access without exposing the devices directly to the internet. This method facilitates secure access to services and resources that would otherwise be inaccessible.
Choosing the right hardware and software for SSH-based remote access is also vital to ensure the security and efficiency of your IoT deployment. A variety of devices are available, each with its strengths and weaknesses. A Raspberry Pi 4 is a versatile and affordable option, providing robust processing power and extensive connectivity options, making it ideal for a wide range of IoT projects. The Arduino Portenta H7 offers high performance and advanced features, designed for professional applications with demanding requirements. The ESP32-S3 is a cost-effective, low-power solution that is well-suited for resource-constrained IoT devices. When selecting an SSH client, consider security features, ease of use, and platform compatibility. Popular options include OpenSSH, PuTTY, and MobaXterm, all of which offer strong encryption and secure authentication protocols. On the server-side, you'll want to use a secure SSH server implementation that is properly configured to adhere to best practices. OpenSSH is a widely-used and highly-regarded option. Proper configuration includes disabling weak ciphers, enabling key-based authentication, and regularly updating the software.
In conclusion, securing remote access to IoT devices is essential for maintaining operational efficiency and protecting sensitive data. SSH is a robust and reliable protocol, providing encrypted communication, strong authentication, and remote command execution capabilities. By understanding the benefits of SSH and implementing best practices such as SSH key authentication, multi-factor authentication, and regular software updates, organizations can significantly improve the security posture of their IoT deployments. Furthermore, by selecting the right hardware and software, you can build a secure, reliable, and easy-to-manage remote access solution that meets the specific needs of your IoT environment. As the IoT landscape continues to evolve, it is crucial to stay informed about the latest security threats and best practices, ensuring that your IoT devices are protected from potential risks.