Are you ready to fortify your Internet of Things (IoT) devices against cyber threats? SSH (Secure Shell) is the unsung hero of IoT security, providing a robust defense against unauthorized access and data breaches, making it an indispensable tool for securing connected devices.
In the rapidly evolving landscape of the Internet of Things (IoT), the need for secure communication and remote access has never been greater. As more and more devices connect to the internet, from smart home appliances to industrial sensors, the potential for cyberattacks increases exponentially. Securing these devices is paramount, and one of the most reliable methods for achieving this is through the use of Secure Shell (SSH). SSH is a cryptographic network protocol that allows for secure communication between two devices over an unsecured network. It provides a secure channel for remote access, command execution, and file transfer, all while encrypting the data to prevent eavesdropping and tampering.
| Category | Details |
|---|---|
| Definition of Secure Shell (SSH) | A cryptographic network protocol for secure communication between two devices, enabling secure remote access, command execution, and file transfer. |
| Functionality within IoT |
|
| Why is SSH Important? |
|
| Default Port for SSH | Port 22 |
| Benefits of Using SSH in IoT |
|
| Best Practices for Securing IoT Devices Using SSH |
|
| Common Issues and Troubleshooting Tips |
|
| SSH in IoT Ecosystems |
SSH integrates seamlessly with various IoT architectures, providing secure access in diverse applications, from smart homes to industrial automation systems. |
| Applications |
|
For more information, you can refer to the official documentation: OpenSSH Official Website.
The integration of SSH within IoT networks addresses critical security concerns and streamlines remote management operations. The ability to establish secure connections is paramount, especially in scenarios where physical access to devices is limited or impractical. SSH facilitates a secure, encrypted channel for remote access, configuration, and monitoring, acting as a cornerstone in protecting sensitive data and preventing unauthorized intrusions. By utilizing SSH, administrators can remotely access, configure, and troubleshoot IoT devices, ensuring that they are running efficiently and securely. This also allows for rapid response to any issues and minimizes downtime. This functionality is crucial for managing and maintaining a large number of connected devices scattered across various locations. SSH allows for efficient management and reduces the need for on-site intervention, saving time and resources.
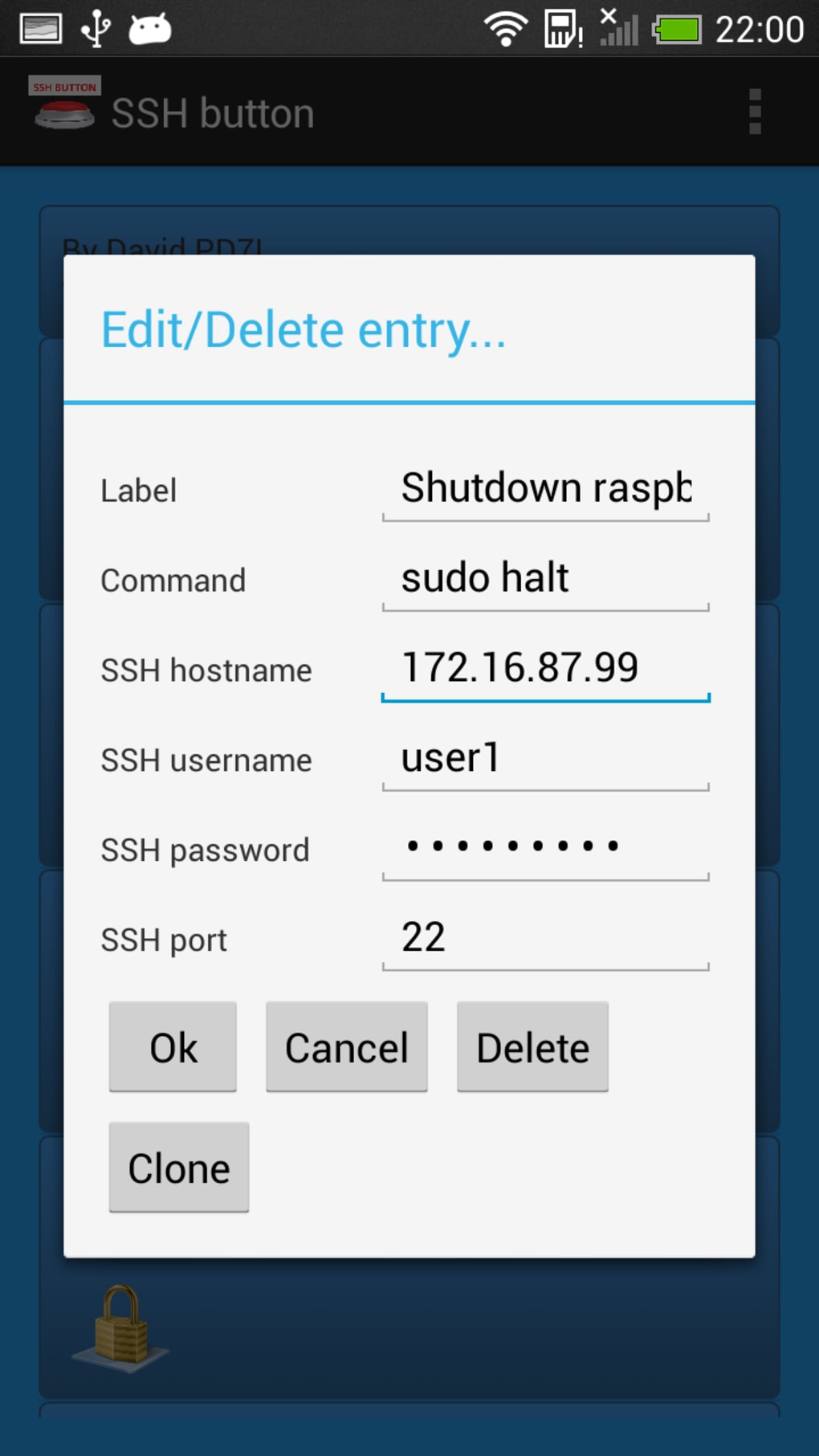
Configuring SSH on an IoT device typically involves installing the SSH server software and enabling it. Once enabled, the device will listen for SSH connections on a specified port (usually port 22). To connect to an IoT device via SSH, you'll need an SSH client, which is readily available on most operating systems, including Linux, macOS, and Windows. The general process involves providing the device's IP address, username, and password (or private key for key-based authentication). The client then establishes an encrypted connection to the device, allowing you to execute commands and transfer files securely.
Key-based authentication is generally considered more secure than password-based authentication. With key-based authentication, instead of using a password, you generate a pair of cryptographic keys: a public key and a private key. The public key is placed on the IoT device, and the private key is kept secure on your client machine. When you attempt to connect, the SSH server on the IoT device uses the public key to verify that you possess the corresponding private key, thus authenticating your identity. This method eliminates the risk of password interception and offers a higher level of security.
While SSH is a powerful tool, it's crucial to implement best practices to ensure its effectiveness in securing IoT devices. One of the first steps is to change the default SSH port. The default port (port 22) is widely known and a common target for attackers. By changing the port to a less obvious one, you can reduce the risk of automated attacks. Another critical measure is to use strong passwords or, ideally, key-based authentication. Strong passwords should be long, complex, and unique. Key-based authentication offers a significant security advantage by eliminating the need for passwords altogether. Additionally, it's essential to disable root login, as logging in as the root user can expose the system to greater risks if the credentials are compromised. Regularly updating SSH software is also crucial. Updates often include security patches that address known vulnerabilities. By keeping your SSH software up-to-date, you ensure that you have the latest security features and protection against known exploits.
Further, it's important to implement firewall rules to restrict access to the SSH port. Firewalls can limit access to the SSH port to only trusted IP addresses or networks, further minimizing the attack surface. Monitoring SSH logs for suspicious activity is another vital aspect of security. Logs can reveal failed login attempts, unusual command executions, and other indicators of potential attacks. By regularly reviewing these logs, you can identify and respond to threats promptly. Another security measure is to consider implementing multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide multiple forms of verification before granting access. This can significantly enhance the security of your IoT devices, especially if a password is compromised.
Troubleshooting SSH connections on IoT devices can sometimes be challenging, but by following a systematic approach, you can often resolve common issues. If you encounter connection refused errors, verify that SSH is enabled on the device and that the correct port is being used. Authentication failures often indicate incorrect usernames or passwords, or problems with SSH key configuration. Firewall issues can also block SSH traffic, so ensure that your firewall allows incoming connections on the SSH port. Network connectivity problems can prevent you from reaching the device, so check your network connection and the device's IP address. Understanding the potential causes of these issues and knowing how to address them is critical for effective IoT device management.
The future of SSH in IoT is bright, with evolving security threats and emerging technologies driving innovation. As IoT devices become more sophisticated and interconnected, the need for secure communication will only increase. New advancements in encryption, authentication, and intrusion detection systems are continually improving SSH security and functionality. Integration with other security protocols and technologies, such as VPNs (Virtual Private Networks) and zero-trust architectures, is likely to further enhance SSH's role in securing IoT networks. The ongoing development and adoption of these advanced security measures will ensure that SSH remains a vital tool in the ever-evolving landscape of IoT security.
In conclusion, SSH is an indispensable tool for securing IoT devices, providing secure remote access, data encryption, and efficient management capabilities. By understanding the fundamentals of SSH, implementing best practices, and staying informed about the latest security trends, you can protect your IoT devices from potential threats and ensure the integrity and confidentiality of your data. As the IoT landscape continues to grow, the importance of SSH will only increase, making it an essential component of any robust IoT security strategy.