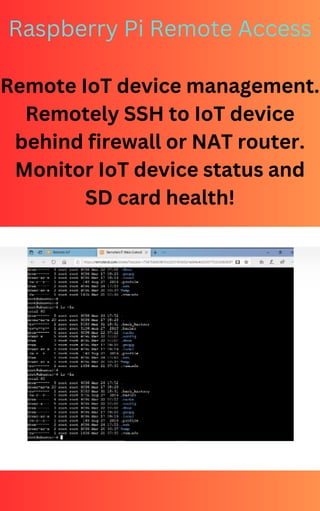
Is secure remote access a cornerstone of modern IoT management? Absolutely. Employing robust methods like Secure Shell (SSH) is paramount in safeguarding devices and sensitive data within the rapidly expanding Internet of Things ecosystem.
SSH, a cryptographic network protocol born in 1995, has evolved into the industry standard for establishing secure communication pathways across networks. Its significance in the realm of IoT is particularly pronounced, given the distributed nature of these devices and the potential vulnerabilities they face. The rise of the Internet of Things has led to unprecedented connectivity, and with this comes an exponential increase in the need for secure and reliable remote access solutions. The challenge lies in providing seamless connectivity without compromising the security of devices and the data they generate. Effective SSH implementation offers a robust solution, providing a secure channel for managing, monitoring, and troubleshooting IoT devices from anywhere in the world.
To fully grasp the landscape of SSH in IoT, one must understand the key players and their respective strengths. The following table provides a comprehensive overview of the leading SSH solutions for IoT device management:
| Feature | Dropbear SSH | OpenSSH | Tailscale SSH | Remote.it | Termius | JuiceSSH | ConnectBot |
|---|---|---|---|---|---|---|---|
| Primary Use | Embedded Systems & Low-Power Devices | General Purpose, Server Management | Secure Peer-to-Peer Connections | Remote Device Access & Management | Cross-Platform SSH Client | Android SSH Client | Android SSH Client |
| Key Advantages | Lightweight, Optimized for resource-constrained devices | Widely used, Feature-rich, Secure by default | Simplified VPN, End-to-end encryption, NAT traversal | Simplified Remote Access, Web-based Management | Intuitive Interface, Cross-Platform Synchronization | User-Friendly Interface, SSH Tunneling | Open-Source, Lightweight, Scripting Support |
| Disadvantages | Limited feature set compared to OpenSSH | Can be resource-intensive on constrained devices | Dependency on Tailscale infrastructure | Subscription-based for advanced features | Subscription required for advanced features, some features are missing | Limited free features. | User Interface is not modern. |
| Security Considerations | Strong encryption, Regular updates | Strong encryption, Regular security audits | End-to-end encryption, Mutual authentication | Secure access, access logging | Secure storage of credentials, Strong encryption | Secure storage of credentials | Secure storage of credentials |
| Ease of Use | Moderate, Requires some configuration | Moderate, Command-line driven | Very Easy, Simple setup | Easy, Web-based configuration | Easy, Intuitive interface | Easy, User-friendly | Easy, User-friendly |
| Platform Support | Embedded Linux, Various platforms | Linux, macOS, Windows, etc. | All major operating systems | All major operating systems | iOS, Android, macOS, Windows, Linux | Android | Android |
| Resource Consumption | Low | Moderate | Low | Moderate | Moderate | Low | Low |
| Licensing | BSD License | Open Source (BSD License) | Proprietary with a free tier | Commercial with a free tier | Freemium | Freemium | Open Source |
| Best Suited For | Resource-constrained IoT devices | General-purpose server management | Connecting devices across different networks | Remote access and management of IoT devices | Remote SSH and general purpose | Remote SSH on Android | Remote SSH on Android |
The utilization of SSH tunneling is a cornerstone of secure remote access, enabling users to establish protected communication channels with remote servers, networks, and devices. This technique employs an assigned port, shielding traffic from potential threats. Effectively, SSH tunneling acts as a secure conduit, allowing internet traffic to traverse between local and remote devices, even in the presence of firewalls and gateway routers.
When selecting an SSH solution for your IoT deployment, it's crucial to consider the specific requirements of your devices and the environment in which they operate. Dropbear SSH stands out as an exceptional choice for low-power IoT devices, owing to its lightweight nature and optimization for embedded systems. Its design prioritizes efficiency, making it ideal for resource-constrained devices where every byte of memory and processing cycle counts. In environments where security is paramount, Dropbear delivers robust encryption and authentication, ensuring the confidentiality and integrity of data transmitted over the network.
OpenSSH is a widely adopted SSH tool, celebrated for its feature-rich capabilities and commitment to robust security. OpenSSH is the cornerstone of secure remote access. Its extensive features and support for a wide range of operating systems make it a versatile solution, and its emphasis on security ensures that connections are protected from unauthorized access. It remains a strong choice for general purpose server management and is often the go-to solution for many system administrators and IT professionals.
Tailscale SSH provides a unique approach to secure connectivity, offering a simplified VPN experience. It simplifies the process of establishing secure connections between devices, especially across different networks, by leveraging end-to-end encryption. This design allows users to traverse NAT (Network Address Translation) and firewall restrictions effortlessly, making it an elegant solution for connecting devices in diverse and complex network environments. This approach reduces the complexity of configuring firewalls and managing network settings, making remote access significantly more streamlined.
Remote.it focuses on simplifying remote device access and management. It offers a user-friendly interface and web-based configuration tools, enabling straightforward access to IoT devices without the need for complex network configurations. This approach reduces the complexities typically associated with remote access, such as firewall rules and port forwarding, and can significantly reduce the time and effort required to manage devices remotely.
Termius, JuiceSSH, and ConnectBot represent prominent SSH client options for Android devices. These tools provide mobile access to remote devices. Termius offers a user-friendly interface and cross-platform synchronization capabilities, enabling seamless access across various devices. JuiceSSH provides a similarly intuitive interface with SSH tunneling functionality. ConnectBot, an open-source option, delivers a lightweight solution with scripting support. The availability of strong SSH clients for Android empowers users to manage their IoT devices from anywhere.
The core function of any SSH solution for IoT is to create a secure tunnel, thereby protecting data from eavesdropping and unauthorized access. Encryption is a fundamental pillar of SSH, ensuring that data transmitted between devices remains confidential. Authentication mechanisms, such as passwords and SSH keys, verify the identity of users and devices, preventing unauthorized access. It's also critical to keep the SSH server software updated, as updates often include security patches that address vulnerabilities. Regular security audits can also help to identify and address potential weaknesses in the system.
IoT device security is not a one-size-fits-all solution; it requires a layered approach. The best remote IoT device SSH solutions play a crucial role in safeguarding connections, preserving data privacy, and streamlining device management. Implementing SSH in your IoT infrastructure is a critical step towards building a secure and reliable system. Furthermore, it allows you to manage your devices and gain insight into their operation from any location.
The future of SSH in IoT is bright, with ongoing advancements in security and performance. As IoT ecosystems become more complex, the need for robust remote access solutions will only intensify. Developers are working on more efficient and secure SSH implementations, and improvements in authentication and key management are also on the horizon. The ongoing integration of SSH with emerging technologies, such as edge computing and 5G, will further enhance the capabilities and applicability of SSH in IoT. The evolution of SSH will continue to play a vital role in securing and enabling the vast network of interconnected devices that form the modern IoT landscape.
In conclusion, securing your IoT devices begins with choosing the right SSH solution. By understanding the strengths of the various options available, you can make an informed decision that protects your devices, preserves data privacy, and streamlines your device management. Through the use of technologies like SSH, it is possible to build a more connected, secure, and efficient future.
For further detailed information and best practices, refer to trusted resources like the OpenSSH official website.