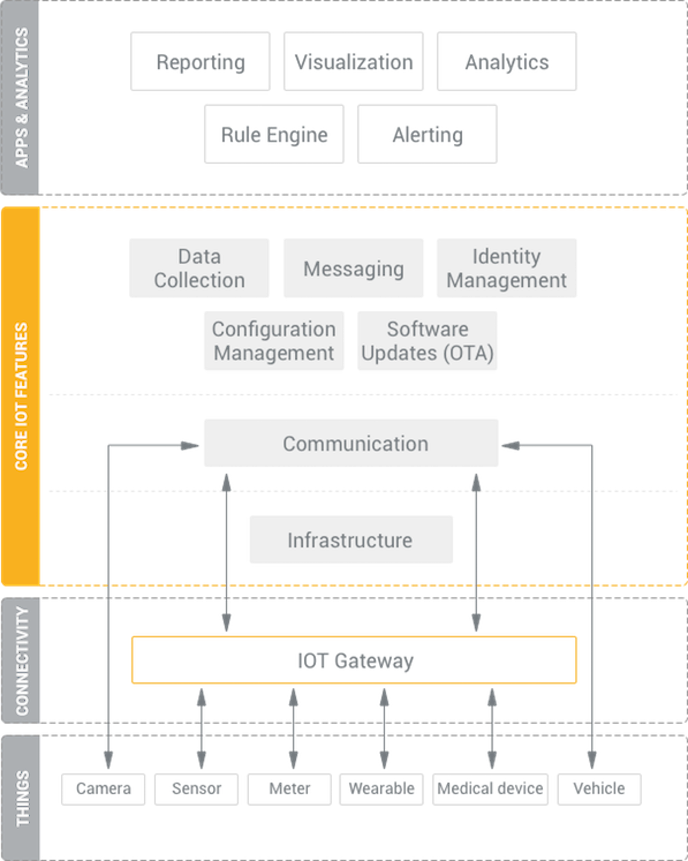
Is your Raspberry Pi stubbornly refusing to connect remotely, leaving you locked out of your IoT projects? The inability to access your Raspberry Pi via SSH, especially when you're relying on key-based authentication, can grind your operations to a halt. This issue is a common frustration, but fear not; we'll explore the intricacies of SSH key authentication and guide you through troubleshooting and resolution.
The world of the Internet of Things (IoT) is rapidly expanding, and with it comes the need for secure, remote access to your devices. Secure Shell (SSH) keys are the preferred method for accessing devices, including Raspberry Pis, because they eliminate the need for password-based authentication, which is vulnerable to brute-force attacks. When your remote IoT platform's SSH key fails to function, it’s a critical issue that requires immediate attention. Let's explore the common causes and fixes for this frustrating problem, ensuring your projects remain accessible and secure.
Let's delve into the specifics of troubleshooting SSH key failures on your Raspberry Pi, uncovering the potential causes and providing practical solutions.
| Aspect | Details |
|---|---|
| Problem | Remote IoT Platform SSH Key Not Working on Raspberry Pi |
| Impact | Inability to remotely access and manage the Raspberry Pi, disrupting IoT projects and workflows. |
| Common Causes |
|
| Solutions |
|
| Step-by-Step Guide |
|
| Security Considerations |
|
| Resources | Raspberry Pi Foundation - Remote Access Documentation |
The default SSH key management systems can sometimes be complex, and that complexity can expose your system to potential attacks. However, modern remote IoT platforms provide streamlined SSH key management, allowing you to centralize the management of all authentication keys and login files. This enhances overall security and simplifies administrative tasks.
When tackling the issue of “SSH Raspberry Pi IoT from anywhere not working,” several factors should be considered. One of the most frequent culprits is an incorrect network configuration. If your Raspberry Pi can't establish a connection with the outside world, remote access will be impossible. Check your router's settings, ensure port forwarding is configured correctly (typically forwarding port 22 to the Raspberry Pi's internal IP address), and that your firewall isn't blocking SSH traffic.
One of the first steps is to verify the SSH key pair itself. This involves ensuring that your keys are intact and correct. You can generate a new key pair using the command `ssh-keygen`. This creates a public and private key pair that enables secure communication. Once the keys are generated, you need to copy the public key (the one with the `.pub` extension) to the `~/.ssh/authorized_keys` file on your Raspberry Pi. If this step is performed incorrectly, your SSH key authentication will fail.
Another key aspect of remote SSH access is the network configuration. If you're attempting to connect to your Raspberry Pi from outside your local network, port forwarding on your router is essential. Port forwarding directs incoming traffic on a specific port (typically port 22 for SSH) to the Raspberry Pi's internal IP address. Without proper port forwarding, the connection won't be established. Confirm that the port forwarding rules are correctly configured. You will also want to ensure that the Raspberry Pi's firewall is not blocking SSH traffic. Tools like `ufw` (Uncomplicated Firewall) can be used to manage the firewall.
The SSH service itself must be running correctly. Check the service status on your Raspberry Pi by using the command `sudo systemctl status ssh`. If the service isn't running, start it with `sudo systemctl start ssh`. If the service fails to start, examine the logs (usually found in `/var/log/auth.log` or `/var/log/syslog`) for error messages that may provide clues about the problem. You might also need to restart the SSH service using the command `sudo systemctl restart ssh` after making changes to its configuration.
Sometimes, the problem is not with the keys, the network, or the service, but with file permissions. The `~/.ssh` directory on your Raspberry Pi should have permissions set to `700` (drwx------), and the `authorized_keys` file within should have permissions set to `600` (-rw-------). Incorrect permissions can prevent the SSH server from accessing the public key and authenticating your connection. Use `chmod` to adjust permissions as needed. For example, `chmod 700 ~/.ssh` and `chmod 600 ~/.ssh/authorized_keys`.
When diagnosing IoT platform remote SSH not working, understand that the root cause can be a combination of factors. The first step is often to verify the SSH key pair. Confirm that the public key is correctly appended to the `authorized_keys` file. Then, review your network configuration, especially port forwarding if you are accessing your Raspberry Pi remotely. Also, ensure the SSH service is running and properly configured. Check the logs, particularly `/var/log/auth.log`, for any errors that might indicate the problem.
Let's consider a step-by-step guide to troubleshooting: First, generate a new SSH key pair on your local machine. Then, copy the public key to the Raspberry Pi's `authorized_keys` file. Next, confirm the Raspberry Pi's IP address and, if accessing remotely, verify port forwarding on your router. Ensure that the SSH service is active, and check the permissions of the `~/.ssh` directory and `authorized_keys` file. Finally, test the connection from your local machine using `ssh pi@
For added security, consider disabling password-based authentication. This will force you to use key-based authentication, which is significantly more secure. You can also set up fail2ban to help protect against brute-force attacks. Regularly update your Raspberry Pi's operating system and any security software to patch vulnerabilities.
Managing smart home devices, monitoring sensors, or automating tasks often hinges on SSH. When SSH Raspberry Pi IoT from anywhere not working becomes a roadblock, it disrupts your entire workflow. Pinpointing the issue is crucial. Begin by verifying the key pair, double-checking network configurations, and confirming the SSH service is running. Pay attention to any error messages during the connection attempts; they often hold valuable clues. Troubleshooting may involve checking the SSH configuration file (`/etc/ssh/sshd_config`) for any restrictive settings.
Remote access is vital for managing and maintaining your IoT devices. However, it also opens the door to security risks. Incorrect SSH key management can be exploited. Implement strong security practices, such as using unique passphrases for your private keys and regularly updating your system. Disable password authentication to prevent brute-force attacks. Be aware of potential vulnerabilities and take measures to safeguard your Raspberry Pi and the data it handles.
If you are still experiencing difficulties, consider reviewing the official Raspberry Pi documentation and online forums for further assistance. The Raspberry Pi community is usually willing to help. Remember that persistence and careful attention to detail are crucial when troubleshooting SSH key issues. By methodically working through the steps, you can often pinpoint the root cause and restore your remote access capabilities.
For enhanced security and ease of management, explore platforms that offer streamlined SSH key management. These platforms allow you to centralize and control all authentication keys and login files, simplifying administration and bolstering your defenses. This is particularly important for IoT projects that may involve multiple devices.